End user security can be enforced at multiple levels. The levels are as under:
1. Server level : This controls whether an end user can connect to the Analysis server with a client application.
2. Database level: Defines the databases that the end user can view on the Analysis server
3. Cube/Mining model level: Defines the cubes or mining models a connected end user can view.
4. Dimension Level: This defines the dimension members that can be viewed by an end user connected to the Analysis server.
5. Cell Level: Defines the cube cells that a connected end user can access. It also sets the read/write permissions for write enabled cubes and limits the cells that an end user can update.
Creating Users and Groups in the Operating system (Windows 2000)
Security in Analysis server is determined by the operating system User and Group accounts. The first step in giving the user access to database and database objects is the creation of the user account in the operating system. User accounts have to be created in the same domain in which the Analysis server is installed or in a trusted domain in which the Analysis server is a member.
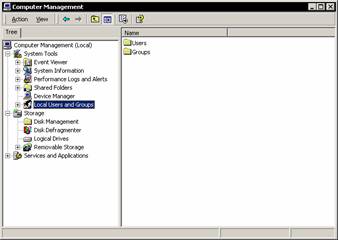
In Windows 2000 Click Settings > Control Panel > Administrative tools > Computer management >Local users and groups. Within the user manager new users and groups can be created.
|
|
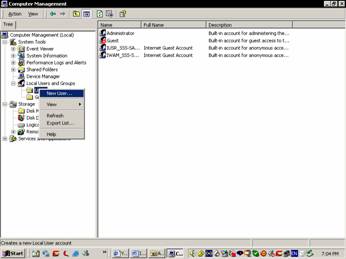
Right click the user folder and select New user…
|
|
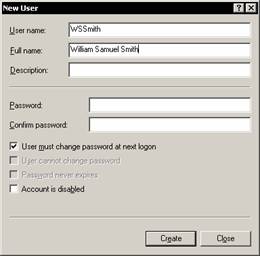
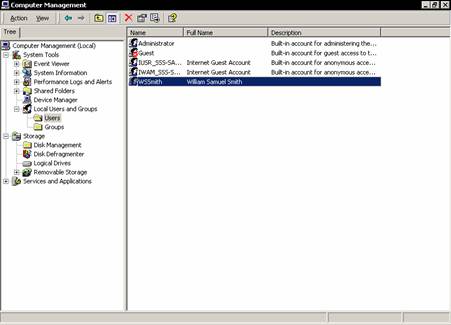
Type in the name of the user. In this case WSSmith. Type in the full name as William Samuel Smith. Let us leave the password text box empty and insist that the user must change his password by checking the check box. Then click Create button. Note that a new user is added to the users.
|
|
{mospagebreak}
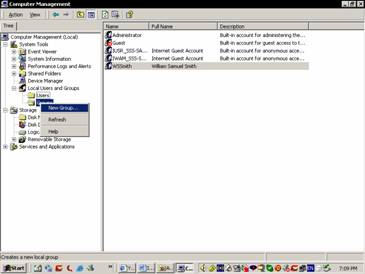
Let us now add a new group to the groups folder. Right click the Groups folder and select New Group
|
|
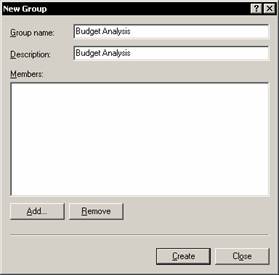
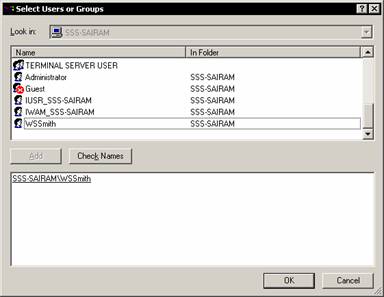
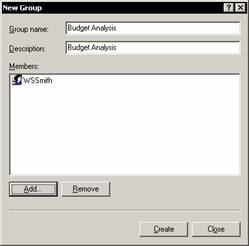
Enter Budget Analysis as the group name and description and click Add button under the members text box. Select WSSmith as the user to be added to this group and Click OK. Note that WSSmith is added as a user of this group.
|
|
Now we close the computer manager window and proceed to creating the same group in Analysis services.
[catlist id=181].